ISO 27001:2013 Information Security Management System
- Home
- ISO 27001:2013 Information Security Management System








ISO 27001 – A tool to demonstrate Business Information Security arrangements
When it comes to keeping information assets secure, organizations can rely on the ISO/IEC 27000 family.
ISO/IEC 27001:2013 specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system within the context of the organization.
It also includes requirements for the assessment and treatment of information security risks tailored to the needs of the organization. The requirements set out in ISO/IEC 27001:2013 are generic and are intended to be applicable to all organizations, regardless of type, size or nature.
SNR Certification – Your partner for ISO 27001 Certification
SNR certification is offering ISO 27001 accredited (UKAS Accreditation Number 8327) certification services to valuable clients since many years. SNR Certification has long list of satisfied clients in more than 30 countries. We have the competence & clientele in all IT & Communication business sectors like:

ISO provide certification or conformity assessment. You’ll need to contact an external certification body for that.
ISO 45001 A tool to show Business Concerns on Human Life & well being.
ISO 9001 is the ISO’s most known standard due to its applicability on all businesses, flexible approach.
ISO 14001 is an internationally agreed standard that sets out the requirements for an EMS.
ISO 22000 sets out the requirements for a food safety management system and can be certified to it.
When it comes to keeping information assets secure, organizations can rely on the ISO/IEC 27000 family.
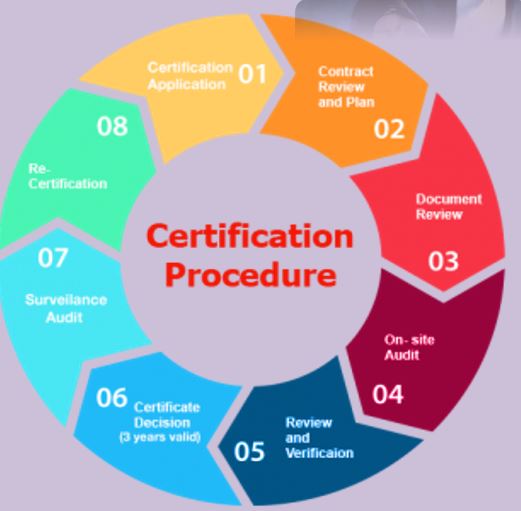
ISO/IEC 27001:2013 specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system.
The organisation shall determine external and internal issues that are relevant to its purpose and that affect its ability to achieve the intended outcome(s) of its information security management system.
This leadership focused clause of ISO 27001 emphasizes the importance of information security being supported, both visibly and materially, by senior management.
You must ensure that the ISMS (information security management system) can achieve its intended outcomes (which should be defined as part of your work conforming with Clause 4), while also preventing or reducing undesired side effects.



